diff --git a/README.md b/README.md
index e7f2ab7..38c48fc 100644
--- a/README.md
+++ b/README.md
@@ -1,21 +1,32 @@
-# keccak-chain-sonobe
+# hash-chain-sonobe
-Repo showcasing usage of [Sonobe](https://github.com/privacy-scaling-explorations/sonobe) with [Circom](https://github.com/iden3/circom) circuits.
-
-Proves a chain of keccak256 hashes, using the [vocdoni/keccak256-circom](https://github.com/vocdoni/keccak256-circom) circuit, with [Nova](https://eprint.iacr.org/2021/370.pdf)+[CycleFold](https://eprint.iacr.org/2023/1192.pdf).
+Repo showcasing usage of [Sonobe](https://github.com/privacy-scaling-explorations/sonobe) with [Arkworks](https://github.com/arkworks-rs) and [Circom](https://github.com/iden3/circom) circuits.
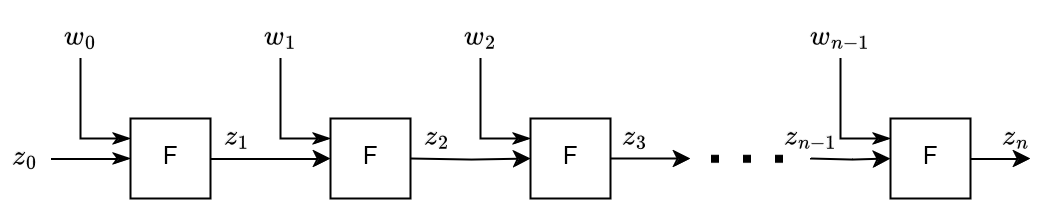
The main idea is to prove $z_n = H(H(...~H(H(H(z_0)))))$, where $n$ is the number of Keccak256 hashes ($H$) that we compute. Proving this in a 'normal' R1CS circuit for a large $n$ would be too costly, but with folding we can manage to prove it in a reasonable time span.
For more info about Sonobe, check out [Sonobe's docs](https://privacy-scaling-explorations.github.io/sonobe-docs).
+
+  +
+
+
+
### Usage
-Assuming rust and circom have been installed:
+### sha_chain.rs (arkworks circuit)
+Proves a chain of SHA256 hashes, using the [arkworks/sha256](https://github.com/arkworks-rs/crypto-primitives/blob/main/crypto-primitives/src/crh/sha256/constraints.rs) circuit, with [Nova](https://eprint.iacr.org/2021/370.pdf)+[CycleFold](https://eprint.iacr.org/2023/1192.pdf).
+- `cargo test --release sha_chain -- --nocapture`
+
+### keccak_chain.rs (circom circuit)
+Proves a chain of keccak256 hashes, using the [vocdoni/keccak256-circom](https://github.com/vocdoni/keccak256-circom) circuit, with [Nova](https://eprint.iacr.org/2021/370.pdf)+[CycleFold](https://eprint.iacr.org/2023/1192.pdf).
+
+Assuming rust and circom have been installed:
- `./compile-circuit.sh`
-- `cargo test --release -- --nocapture`
+- `cargo test --release keccak_chain -- --nocapture`
+
+Note: the Circom variant currently has a bit of extra overhead since at each folding step it uses Circom witness generation to obtain the witness and then it imports it into the arkworks constraint system.
### Repo structure
-- the Circom circuit to be folded is defined at [./circuit/keccak-chain.circom](https://github.com/arnaucube/keccak-chain-sonobe/blob/main/circuit/keccak-chain.circom)
-- the logic to fold the circuit using Sonobe is defined at [src/lib.rs](https://github.com/arnaucube/keccak-chain-sonobe/blob/main/src/lib.rs)
- - (it contains some extra sanity check that would not be needed in a real-world use case)
+- the Circom circuit (that defines the keccak-chain) to be folded is defined at [./circuit/keccak-chain.circom](https://github.com/arnaucube/hash-chain-sonobe/blob/main/circuit/keccak-chain.circom)
+- the logic to fold the circuit using Sonobe is defined at [src/{sha_chain, keccak_chain}.rs](https://github.com/arnaucube/hash-chain-sonobe/blob/main/src)
diff --git a/src/keccak_chain.rs b/src/keccak_chain.rs
new file mode 100644
index 0000000..20b540a
--- /dev/null
+++ b/src/keccak_chain.rs
@@ -0,0 +1,237 @@
+///
+/// This example performs the full flow:
+/// - define the circuit to be folded
+/// - fold the circuit with Nova+CycleFold's IVC
+/// - generate a DeciderEthCircuit final proof
+/// - generate the Solidity contract that verifies the proof
+/// - verify the proof in the EVM
+///
+
+#[cfg(test)]
+mod tests {
+ use ark_bn254::{constraints::GVar, Bn254, Fr, G1Projective as G1};
+ use ark_grumpkin::{constraints::GVar as GVar2, Projective as G2};
+
+ use ark_groth16::Groth16;
+
+ use ark_ff::PrimeField;
+
+ use std::path::PathBuf;
+ use std::rc::Rc;
+ use std::time::Instant;
+
+ use folding_schemes::{
+ commitment::{kzg::KZG, pedersen::Pedersen},
+ folding::nova::{
+ decider_eth::{prepare_calldata, Decider as DeciderEth},
+ Nova, PreprocessorParam,
+ },
+ frontend::{circom::CircomFCircuit, FCircuit},
+ transcript::poseidon::poseidon_canonical_config,
+ Decider, Error, FoldingScheme,
+ };
+ use solidity_verifiers::{
+ utils::get_function_selector_for_nova_cyclefold_verifier,
+ verifiers::nova_cyclefold::get_decider_template_for_cyclefold_decider,
+ NovaCycleFoldVerifierKey,
+ };
+
+ use crate::utils::tests::*;
+
+ // function to compute the next state of the folding via rust-native code (not Circom). Used to
+ // check the Circom values.
+ use tiny_keccak::{Hasher, Keccak};
+ fn rust_native_step(
+ _i: usize,
+ z_i: Vec,
+ _external_inputs: Vec,
+ ) -> Result, Error> {
+ let b = f_vec_bits_to_bytes(z_i.to_vec());
+ let mut h = Keccak::v256();
+ h.update(&b);
+ let mut z_i1 = [0u8; 32];
+ h.finalize(&mut z_i1);
+ bytes_to_f_vec_bits(z_i1.to_vec())
+ }
+
+ #[test]
+ fn full_flow() {
+ // set how many steps of folding we want to compute
+ let n_steps = 1000;
+
+ // set the initial state
+ let z_0_aux: Vec = vec![0_u32; 32 * 8];
+ let z_0: Vec = z_0_aux.iter().map(|v| Fr::from(*v)).collect::>();
+
+ // initialize the Circom circuit
+ let r1cs_path = PathBuf::from("./circuit/keccak-chain.r1cs");
+ let wasm_path = PathBuf::from("./circuit/keccak-chain_js/keccak-chain.wasm");
+
+ let f_circuit_params = (r1cs_path, wasm_path, 32 * 8, 0);
+ let mut f_circuit = CircomFCircuit::::new(f_circuit_params).unwrap();
+ // Note (optional): for more speed, we can set a custom rust-native logic, which will be
+ // used for the `step_native` method instead of extracting the values from the circom
+ // witness:
+ f_circuit.set_custom_step_native(Rc::new(rust_native_step));
+
+ // ----------------
+ // Sanity check
+ // check that the f_circuit produces valid R1CS constraints
+ use ark_r1cs_std::alloc::AllocVar;
+ use ark_r1cs_std::fields::fp::FpVar;
+ use ark_r1cs_std::R1CSVar;
+ use ark_relations::r1cs::ConstraintSystem;
+ let cs = ConstraintSystem::::new_ref();
+ let z_0_var = Vec::>::new_witness(cs.clone(), || Ok(z_0.clone())).unwrap();
+ let z_1_var = f_circuit
+ .generate_step_constraints(cs.clone(), 1, z_0_var, vec![])
+ .unwrap();
+ // check z_1_var against the native z_1
+ let z_1_native = f_circuit.step_native(1, z_0.clone(), vec![]).unwrap();
+ assert_eq!(z_1_var.value().unwrap(), z_1_native);
+ // check that the constraint system is satisfied
+ assert!(cs.is_satisfied().unwrap());
+ // ----------------
+
+ // define type aliases to avoid writting the whole type each time
+ pub type N =
+ Nova, KZG<'static, Bn254>, Pedersen, false>;
+ pub type D = DeciderEth<
+ G1,
+ GVar,
+ G2,
+ GVar2,
+ CircomFCircuit,
+ KZG<'static, Bn254>,
+ Pedersen,
+ Groth16,
+ N,
+ >;
+
+ let poseidon_config = poseidon_canonical_config::();
+ let mut rng = rand::rngs::OsRng;
+
+ // prepare the Nova prover & verifier params
+ let nova_preprocess_params = PreprocessorParam::new(poseidon_config, f_circuit.clone());
+ let start = Instant::now();
+ let nova_params = N::preprocess(&mut rng, &nova_preprocess_params).unwrap();
+ println!("Nova params generated: {:?}", start.elapsed());
+
+ // initialize the folding scheme engine, in our case we use Nova
+ let mut nova = N::init(&nova_params, f_circuit.clone(), z_0.clone()).unwrap();
+
+ // prepare the Decider prover & verifier params
+ let start = Instant::now();
+ let (decider_pp, decider_vp) = D::preprocess(&mut rng, &nova_params, nova.clone()).unwrap();
+ println!("Decider params generated: {:?}", start.elapsed());
+
+ // run n steps of the folding iteration
+ let start_full = Instant::now();
+ for _ in 0..n_steps {
+ let start = Instant::now();
+ nova.prove_step(rng, vec![], None).unwrap();
+ println!(
+ "Nova::prove_step (keccak256 through Circom) {}: {:?}",
+ nova.i,
+ start.elapsed()
+ );
+ }
+ println!("Nova's all steps time: {:?}", start_full.elapsed());
+
+ // perform the hash chain natively in rust (which uses a rust Keccak256 library)
+ let mut z_i_native = z_0.clone();
+ for i in 0..n_steps {
+ z_i_native = rust_native_step(i, z_i_native.clone(), vec![]).unwrap();
+ }
+ // check that the value of the last folding state (nova.z_i) computed through folding, is
+ // equal to the natively computed hash using the rust_native_step method
+ assert_eq!(nova.z_i, z_i_native);
+
+ // ----------------
+ // Sanity check
+ // The following lines contain a sanity check that checks the IVC proof (before going into
+ // the zkSNARK proof)
+ let (running_instance, incoming_instance, cyclefold_instance) = nova.instances();
+ N::verify(
+ nova_params.1, // Nova's verifier params
+ z_0,
+ nova.z_i.clone(),
+ nova.i,
+ running_instance,
+ incoming_instance,
+ cyclefold_instance,
+ )
+ .unwrap();
+ // ----------------
+
+ let rng = rand::rngs::OsRng;
+ let start = Instant::now();
+ let proof = D::prove(rng, decider_pp, nova.clone()).unwrap();
+ println!("generated Decider proof: {:?}", start.elapsed());
+
+ let verified = D::verify(
+ decider_vp.clone(),
+ nova.i,
+ nova.z_0.clone(),
+ nova.z_i.clone(),
+ &nova.U_i,
+ &nova.u_i,
+ &proof,
+ )
+ .unwrap();
+ assert!(verified);
+ println!("Decider proof verification: {}", verified);
+
+ // generate the Solidity code that verifies this Decider final proof
+ let function_selector =
+ get_function_selector_for_nova_cyclefold_verifier(nova.z_0.len() * 2 + 1);
+
+ let calldata: Vec = prepare_calldata(
+ function_selector,
+ nova.i,
+ nova.z_0,
+ nova.z_i,
+ &nova.U_i,
+ &nova.u_i,
+ proof,
+ )
+ .unwrap();
+
+ // prepare the setup params for the solidity verifier
+ let nova_cyclefold_vk = NovaCycleFoldVerifierKey::from((decider_vp, f_circuit.state_len()));
+
+ // generate the solidity code
+ let decider_solidity_code = get_decider_template_for_cyclefold_decider(nova_cyclefold_vk);
+
+ /*
+ * Note: since we're proving the Keccak256 (ie. 32 byte size, 256 bits), the number of
+ * inputs is too big for the contract. In a real world use case we would convert the binary
+ * representation into a couple of field elements which would be inputs of the Decider
+ * circuit, and in-circuit we would obtain the binary representation to be used for the
+ * final proof check.
+ *
+ * The following code is commented out for that reason.
+ // verify the proof against the solidity code in the EVM
+ use solidity_verifiers::evm::{compile_solidity, Evm};
+ let nova_cyclefold_verifier_bytecode =
+ compile_solidity(&decider_solidity_code, "NovaDecider");
+ let mut evm = Evm::default();
+ let verifier_address = evm.create(nova_cyclefold_verifier_bytecode);
+ let (_, output) = evm.call(verifier_address, calldata.clone());
+ assert_eq!(*output.last().unwrap(), 1);
+ */
+
+ // save smart contract and the calldata
+ println!("storing nova-verifier.sol and the calldata into files");
+ use std::fs;
+ fs::create_dir_all("./solidity").unwrap();
+ fs::write(
+ "./solidity/nova-verifier.sol",
+ decider_solidity_code.clone(),
+ )
+ .unwrap();
+ fs::write("./solidity/solidity-calldata.calldata", calldata.clone()).unwrap();
+ let s = solidity_verifiers::utils::get_formatted_calldata(calldata.clone());
+ fs::write("./solidity/solidity-calldata.inputs", s.join(",\n")).expect("");
+ }
+}
diff --git a/src/lib.rs b/src/lib.rs
index 240f950..908318f 100644
--- a/src/lib.rs
+++ b/src/lib.rs
@@ -1,259 +1,7 @@
#![allow(non_snake_case)]
#![allow(non_camel_case_types)]
#![allow(clippy::upper_case_acronyms)]
-///
-/// This example performs the full flow:
-/// - define the circuit to be folded
-/// - fold the circuit with Nova+CycleFold's IVC
-/// - generate a DeciderEthCircuit final proof
-/// - generate the Solidity contract that verifies the proof
-/// - verify the proof in the EVM
-///
-#[cfg(test)]
-mod tests {
- use ark_bn254::{constraints::GVar, Bn254, Fr, G1Projective as G1};
- use ark_grumpkin::{constraints::GVar as GVar2, Projective as G2};
-
- use ark_groth16::Groth16;
-
- use ark_ff::{BigInteger, BigInteger256, PrimeField};
-
- use std::path::PathBuf;
- use std::rc::Rc;
- use std::time::Instant;
-
- use folding_schemes::{
- commitment::{kzg::KZG, pedersen::Pedersen},
- folding::nova::{
- decider_eth::{prepare_calldata, Decider as DeciderEth},
- Nova, PreprocessorParam,
- },
- frontend::{circom::CircomFCircuit, FCircuit},
- transcript::poseidon::poseidon_canonical_config,
- Decider, Error, FoldingScheme,
- };
- use solidity_verifiers::{
- utils::get_function_selector_for_nova_cyclefold_verifier,
- verifiers::nova_cyclefold::get_decider_template_for_cyclefold_decider,
- NovaCycleFoldVerifierKey,
- };
-
- fn f_vec_to_bits(v: Vec) -> Vec {
- v.iter()
- .map(|v_i| {
- if v_i.is_one() {
- return true;
- }
- false
- })
- .collect()
- }
- // returns the bytes representation of the given vector of finite field elements that represent
- // bits
- fn f_vec_to_bytes(v: Vec) -> Vec {
- let b = f_vec_to_bits(v);
- BigInteger256::from_bits_le(&b).to_bytes_le()
- }
- fn bytes_to_f_vec(b: Vec) -> Result, Error> {
- use num_bigint::BigUint;
- let bi = BigUint::from_bytes_le(&b);
- let bi = BigInteger256::try_from(bi).unwrap();
- let bits = bi.to_bits_le();
- Ok(bits
- .iter()
- .map(|&e| if e { F::one() } else { F::zero() })
- .collect())
- }
-
- // function to compute the next state of the folding via rust-native code (not Circom). Used to
- // check the Circom values.
- use tiny_keccak::{Hasher, Keccak};
- fn rust_native_step(
- _i: usize,
- z_i: Vec,
- _external_inputs: Vec,
- ) -> Result, Error> {
- let b = f_vec_to_bytes(z_i.to_vec());
- let mut h = Keccak::v256();
- h.update(&b);
- let mut z_i1 = [0u8; 32];
- h.finalize(&mut z_i1);
- bytes_to_f_vec(z_i1.to_vec())
- }
-
- #[test]
- fn full_flow() {
- // set how many steps of folding we want to compute
- let n_steps = 10;
-
- // set the initial state
- let z_0_aux: Vec = vec![0_u32; 32 * 8];
- let z_0: Vec = z_0_aux.iter().map(|v| Fr::from(*v)).collect::>();
-
- // initialize the Circom circuit
- let r1cs_path = PathBuf::from("./circuit/keccak-chain.r1cs");
- let wasm_path = PathBuf::from("./circuit/keccak-chain_js/keccak-chain.wasm");
-
- let f_circuit_params = (r1cs_path, wasm_path, 32 * 8, 0);
- let mut f_circuit = CircomFCircuit::::new(f_circuit_params).unwrap();
- // Note (optional): for more speed, we can set a custom rust-native logic, which will be
- // used for the `step_native` method instead of extracting the values from the circom
- // witness:
- f_circuit.set_custom_step_native(Rc::new(rust_native_step));
-
- // ----------------
- // Sanity check
- // check that the f_circuit produces valid R1CS constraints
- use ark_r1cs_std::alloc::AllocVar;
- use ark_r1cs_std::fields::fp::FpVar;
- use ark_r1cs_std::R1CSVar;
- use ark_relations::r1cs::ConstraintSystem;
- let cs = ConstraintSystem::::new_ref();
- let z_0_var = Vec::>::new_witness(cs.clone(), || Ok(z_0.clone())).unwrap();
- let z_1_var = f_circuit
- .generate_step_constraints(cs.clone(), 1, z_0_var, vec![])
- .unwrap();
- // check z_1_var against the native z_1
- let z_1_native = f_circuit.step_native(1, z_0.clone(), vec![]).unwrap();
- assert_eq!(z_1_var.value().unwrap(), z_1_native);
- // check that the constraint system is satisfied
- assert!(cs.is_satisfied().unwrap());
- // ----------------
-
- // define type aliases to avoid writting the whole type each time
- pub type N =
- Nova, KZG<'static, Bn254>, Pedersen, false>;
- pub type D = DeciderEth<
- G1,
- GVar,
- G2,
- GVar2,
- CircomFCircuit,
- KZG<'static, Bn254>,
- Pedersen,
- Groth16,
- N,
- >;
-
- let poseidon_config = poseidon_canonical_config::();
- let mut rng = rand::rngs::OsRng;
-
- // prepare the Nova prover & verifier params
- let nova_preprocess_params = PreprocessorParam::new(poseidon_config, f_circuit.clone());
- let start = Instant::now();
- let nova_params = N::preprocess(&mut rng, &nova_preprocess_params).unwrap();
- println!("Nova params generated: {:?}", start.elapsed());
-
- // initialize the folding scheme engine, in our case we use Nova
- let mut nova = N::init(&nova_params, f_circuit.clone(), z_0.clone()).unwrap();
-
- // prepare the Decider prover & verifier params
- let start = Instant::now();
- let (decider_pp, decider_vp) = D::preprocess(&mut rng, &nova_params, nova.clone()).unwrap();
- println!("Decider params generated: {:?}", start.elapsed());
-
- // run n steps of the folding iteration
- for _ in 0..n_steps {
- let start = Instant::now();
- nova.prove_step(rng, vec![], None).unwrap();
- println!("Nova::prove_step {}: {:?}", nova.i, start.elapsed());
- }
-
- // perform the hash chain natively in rust (which uses a rust Keccak256 library)
- let mut z_i_native = z_0.clone();
- for i in 0..n_steps {
- z_i_native = rust_native_step(i, z_i_native.clone(), vec![]).unwrap();
- }
- // check that the value of the last folding state (nova.z_i) computed through folding, is
- // equal to the natively computed hash using the rust_native_step method
- assert_eq!(nova.z_i, z_i_native);
-
- // ----------------
- // Sanity check
- // The following lines contain a sanity check that checks the IVC proof (before going into
- // the zkSNARK proof)
- let (running_instance, incoming_instance, cyclefold_instance) = nova.instances();
- N::verify(
- nova_params.1, // Nova's verifier params
- z_0,
- nova.z_i.clone(),
- nova.i,
- running_instance,
- incoming_instance,
- cyclefold_instance,
- )
- .unwrap();
- // ----------------
-
- let rng = rand::rngs::OsRng;
- let start = Instant::now();
- let proof = D::prove(rng, decider_pp, nova.clone()).unwrap();
- println!("generated Decider proof: {:?}", start.elapsed());
-
- let verified = D::verify(
- decider_vp.clone(),
- nova.i,
- nova.z_0.clone(),
- nova.z_i.clone(),
- &nova.U_i,
- &nova.u_i,
- &proof,
- )
- .unwrap();
- assert!(verified);
- println!("Decider proof verification: {}", verified);
-
- // generate the Solidity code that verifies this Decider final proof
- let function_selector =
- get_function_selector_for_nova_cyclefold_verifier(nova.z_0.len() * 2 + 1);
-
- let calldata: Vec = prepare_calldata(
- function_selector,
- nova.i,
- nova.z_0,
- nova.z_i,
- &nova.U_i,
- &nova.u_i,
- proof,
- )
- .unwrap();
-
- // prepare the setup params for the solidity verifier
- let nova_cyclefold_vk = NovaCycleFoldVerifierKey::from((decider_vp, f_circuit.state_len()));
-
- // generate the solidity code
- let decider_solidity_code = get_decider_template_for_cyclefold_decider(nova_cyclefold_vk);
-
- /*
- * Note: since we're proving the Keccak256 (ie. 32 byte size, 256 bits), the number of
- * inputs is too big for the contract. In a real world use case we would convert the binary
- * representation into a couple of field elements which would be inputs of the Decider
- * circuit, and in-circuit we would obtain the binary representation to be used for the
- * final proof check.
- *
- * The following code is commented out for that reason.
- // verify the proof against the solidity code in the EVM
- use solidity_verifiers::evm::{compile_solidity, Evm};
- let nova_cyclefold_verifier_bytecode =
- compile_solidity(&decider_solidity_code, "NovaDecider");
- let mut evm = Evm::default();
- let verifier_address = evm.create(nova_cyclefold_verifier_bytecode);
- let (_, output) = evm.call(verifier_address, calldata.clone());
- assert_eq!(*output.last().unwrap(), 1);
- */
-
- // save smart contract and the calldata
- println!("storing nova-verifier.sol and the calldata into files");
- use std::fs;
- fs::create_dir_all("./solidity").unwrap();
- fs::write(
- "./solidity/nova-verifier.sol",
- decider_solidity_code.clone(),
- )
- .unwrap();
- fs::write("./solidity/solidity-calldata.calldata", calldata.clone()).unwrap();
- let s = solidity_verifiers::utils::get_formatted_calldata(calldata.clone());
- fs::write("./solidity/solidity-calldata.inputs", s.join(",\n")).expect("");
- }
-}
+mod keccak_chain;
+mod sha_chain;
+mod utils;
diff --git a/src/sha_chain.rs b/src/sha_chain.rs
new file mode 100644
index 0000000..4acbb04
--- /dev/null
+++ b/src/sha_chain.rs
@@ -0,0 +1,273 @@
+///
+/// This example performs the full flow:
+/// - define the circuit to be folded
+/// - fold the circuit with Nova+CycleFold's IVC
+/// - generate a DeciderEthCircuit final proof
+/// - generate the Solidity contract that verifies the proof
+/// - verify the proof in the EVM
+///
+
+#[cfg(test)]
+mod tests {
+ use ark_bn254::{constraints::GVar, Bn254, Fr, G1Projective as G1};
+ use ark_grumpkin::{constraints::GVar as GVar2, Projective as G2};
+
+ use ark_groth16::Groth16;
+
+ use ark_ff::PrimeField;
+
+ use std::time::Instant;
+
+ use ark_crypto_primitives::crh::sha256::{constraints::Sha256Gadget, digest::Digest, Sha256};
+ use ark_r1cs_std::fields::fp::FpVar;
+ use ark_r1cs_std::{bits::uint8::UInt8, boolean::Boolean, ToBitsGadget, ToBytesGadget};
+ use ark_relations::r1cs::{ConstraintSystemRef, SynthesisError};
+ use std::marker::PhantomData;
+
+ use folding_schemes::{
+ commitment::{kzg::KZG, pedersen::Pedersen},
+ folding::nova::{
+ decider_eth::{prepare_calldata, Decider as DeciderEth},
+ Nova, PreprocessorParam,
+ },
+ frontend::FCircuit,
+ transcript::poseidon::poseidon_canonical_config,
+ Decider, Error, FoldingScheme,
+ };
+ use solidity_verifiers::{
+ utils::get_function_selector_for_nova_cyclefold_verifier,
+ verifiers::nova_cyclefold::get_decider_template_for_cyclefold_decider,
+ NovaCycleFoldVerifierKey,
+ };
+
+ use crate::utils::tests::*;
+
+ /// Test circuit to be folded
+ #[derive(Clone, Copy, Debug)]
+ pub struct SHA256FoldStepCircuit {
+ _f: PhantomData,
+ }
+ impl FCircuit for SHA256FoldStepCircuit {
+ type Params = ();
+ fn new(_params: Self::Params) -> Result {
+ Ok(Self { _f: PhantomData })
+ }
+ fn state_len(&self) -> usize {
+ 32
+ }
+ fn external_inputs_len(&self) -> usize {
+ 0
+ }
+ // function to compute the next state of the folding via rust-native code (not Circom). Used to
+ // check the Circom values.
+ fn step_native(
+ &self,
+ _i: usize,
+ z_i: Vec,
+ _external_inputs: Vec,
+ ) -> Result, Error> {
+ let b = f_vec_to_bytes(z_i.to_vec());
+ let mut sha256 = Sha256::default();
+ sha256.update(b);
+ let z_i1 = sha256.finalize().to_vec();
+
+ bytes_to_f_vec(z_i1.to_vec())
+ }
+ fn generate_step_constraints(
+ &self,
+ _cs: ConstraintSystemRef,
+ _i: usize,
+ z_i: Vec>,
+ _external_inputs: Vec>,
+ ) -> Result>, SynthesisError> {
+ let mut sha256_var = Sha256Gadget::default();
+ let z_i_u8: Vec> = z_i
+ .iter()
+ .map(|f| UInt8::::from_bits_le(&f.to_bits_le().unwrap()[..8]))
+ .collect::>();
+ sha256_var.update(&z_i_u8).unwrap();
+ let z_i1_u8 = sha256_var.finalize()?.to_bytes()?;
+ let z_i1: Vec> = z_i1_u8
+ .iter()
+ .map(|e| {
+ let bits = e.to_bits_le().unwrap();
+ Boolean::::le_bits_to_fp_var(&bits).unwrap()
+ })
+ .collect();
+
+ Ok(z_i1)
+ }
+ }
+
+ #[test]
+ fn full_flow() {
+ // set how many steps of folding we want to compute
+ let n_steps = 100;
+
+ // set the initial state
+ // let z_0_aux: Vec = vec![0_u32; 32 * 8];
+ let z_0_aux: Vec = vec![0_u8; 32];
+ let z_0: Vec = z_0_aux.iter().map(|v| Fr::from(*v)).collect::>();
+
+ let f_circuit = SHA256FoldStepCircuit::::new(()).unwrap();
+
+ // ----------------
+ // Sanity check
+ // check that the f_circuit produces valid R1CS constraints
+ use ark_r1cs_std::alloc::AllocVar;
+ use ark_r1cs_std::fields::fp::FpVar;
+ use ark_r1cs_std::R1CSVar;
+ use ark_relations::r1cs::ConstraintSystem;
+ let cs = ConstraintSystem::::new_ref();
+ let z_0_var = Vec::>::new_witness(cs.clone(), || Ok(z_0.clone())).unwrap();
+ let z_1_var = f_circuit
+ .generate_step_constraints(cs.clone(), 1, z_0_var, vec![])
+ .unwrap();
+ // check z_1_var against the native z_1
+ let z_1_native = f_circuit.step_native(1, z_0.clone(), vec![]).unwrap();
+ assert_eq!(z_1_var.value().unwrap(), z_1_native);
+ // check that the constraint system is satisfied
+ assert!(cs.is_satisfied().unwrap());
+ // ----------------
+
+ // define type aliases to avoid writting the whole type each time
+ pub type N = Nova<
+ G1,
+ GVar,
+ G2,
+ GVar2,
+ SHA256FoldStepCircuit,
+ KZG<'static, Bn254>,
+ Pedersen,
+ false,
+ >;
+ pub type D = DeciderEth<
+ G1,
+ GVar,
+ G2,
+ GVar2,
+ SHA256FoldStepCircuit,
+ KZG<'static, Bn254>,
+ Pedersen,
+ Groth16,
+ N,
+ >;
+
+ let poseidon_config = poseidon_canonical_config::();
+ let mut rng = rand::rngs::OsRng;
+
+ // prepare the Nova prover & verifier params
+ let nova_preprocess_params = PreprocessorParam::new(poseidon_config, f_circuit);
+ let start = Instant::now();
+ let nova_params = N::preprocess(&mut rng, &nova_preprocess_params).unwrap();
+ println!("Nova params generated: {:?}", start.elapsed());
+
+ // initialize the folding scheme engine, in our case we use Nova
+ let mut nova = N::init(&nova_params, f_circuit, z_0.clone()).unwrap();
+
+ // prepare the Decider prover & verifier params
+ let start = Instant::now();
+ let (decider_pp, decider_vp) = D::preprocess(&mut rng, &nova_params, nova.clone()).unwrap();
+ println!("Decider params generated: {:?}", start.elapsed());
+
+ // run n steps of the folding iteration
+ let start_full = Instant::now();
+ for _ in 0..n_steps {
+ let start = Instant::now();
+ nova.prove_step(rng, vec![], None).unwrap();
+ println!(
+ "Nova::prove_step (sha256) {}: {:?}",
+ nova.i,
+ start.elapsed()
+ );
+ }
+ println!("Nova's all steps time: {:?}", start_full.elapsed());
+
+ // ----------------
+ // Sanity check
+ // The following lines contain a sanity check that checks the IVC proof (before going into
+ // the zkSNARK proof)
+ let (running_instance, incoming_instance, cyclefold_instance) = nova.instances();
+ N::verify(
+ nova_params.1, // Nova's verifier params
+ z_0,
+ nova.z_i.clone(),
+ nova.i,
+ running_instance,
+ incoming_instance,
+ cyclefold_instance,
+ )
+ .unwrap();
+ // ----------------
+
+ let rng = rand::rngs::OsRng;
+ let start = Instant::now();
+ let proof = D::prove(rng, decider_pp, nova.clone()).unwrap();
+ println!("generated Decider proof: {:?}", start.elapsed());
+
+ let verified = D::verify(
+ decider_vp.clone(),
+ nova.i,
+ nova.z_0.clone(),
+ nova.z_i.clone(),
+ &nova.U_i,
+ &nova.u_i,
+ &proof,
+ )
+ .unwrap();
+ assert!(verified);
+ println!("Decider proof verification: {}", verified);
+
+ // generate the Solidity code that verifies this Decider final proof
+ let function_selector =
+ get_function_selector_for_nova_cyclefold_verifier(nova.z_0.len() * 2 + 1);
+
+ let calldata: Vec = prepare_calldata(
+ function_selector,
+ nova.i,
+ nova.z_0,
+ nova.z_i,
+ &nova.U_i,
+ &nova.u_i,
+ proof,
+ )
+ .unwrap();
+
+ // prepare the setup params for the solidity verifier
+ let nova_cyclefold_vk = NovaCycleFoldVerifierKey::from((decider_vp, f_circuit.state_len()));
+
+ // generate the solidity code
+ let decider_solidity_code = get_decider_template_for_cyclefold_decider(nova_cyclefold_vk);
+
+ /*
+ * Note: since we're proving the SHA256 (ie. 32 byte size, 256 bits), the number of inputs
+ * is too big for the contract. In a real world use case we would convert the binary
+ * representation into a couple of field elements which would be inputs of the Decider
+ * circuit, and in-circuit we would obtain the binary representation to be used for the
+ * final proof check.
+ *
+ * The following code is commented out for that reason.
+ // verify the proof against the solidity code in the EVM
+ use solidity_verifiers::evm::{compile_solidity, Evm};
+ let nova_cyclefold_verifier_bytecode =
+ compile_solidity(&decider_solidity_code, "NovaDecider");
+ let mut evm = Evm::default();
+ let verifier_address = evm.create(nova_cyclefold_verifier_bytecode);
+ let (_, output) = evm.call(verifier_address, calldata.clone());
+ assert_eq!(*output.last().unwrap(), 1);
+ */
+
+ // save smart contract and the calldata
+ println!("storing nova-verifier.sol and the calldata into files");
+ use std::fs;
+ fs::create_dir_all("./solidity").unwrap();
+ fs::write(
+ "./solidity/nova-verifier.sol",
+ decider_solidity_code.clone(),
+ )
+ .unwrap();
+ fs::write("./solidity/solidity-calldata.calldata", calldata.clone()).unwrap();
+ let s = solidity_verifiers::utils::get_formatted_calldata(calldata.clone());
+ fs::write("./solidity/solidity-calldata.inputs", s.join(",\n")).expect("");
+ }
+}
diff --git a/src/utils.rs b/src/utils.rs
new file mode 100644
index 0000000..ba32743
--- /dev/null
+++ b/src/utils.rs
@@ -0,0 +1,49 @@
+#[cfg(test)]
+pub(crate) mod tests {
+ use ark_ff::{BigInteger, BigInteger256, PrimeField};
+ use folding_schemes::Error;
+
+ /// interprets the vector of finite field elements as a vector of bytes
+ pub(crate) fn f_vec_to_bytes(b: Vec) -> Vec {
+ b.iter()
+ .map(|e| {
+ let bytes: Vec = e.into_bigint().to_bytes_le();
+ bytes[0]
+ })
+ .collect()
+ }
+ /// for a given byte array, returns the bytes representation in finite field elements
+ pub(crate) fn bytes_to_f_vec(b: Vec) -> Result, Error> {
+ Ok(b.iter()
+ .map(|&e| F::from_le_bytes_mod_order(&[e]))
+ .collect::>())
+ }
+ /// returns the bytes representation of the given vector of finite field elements that represent
+ /// bits
+ pub(crate) fn f_vec_bits_to_bytes(v: Vec) -> Vec {
+ let b = f_vec_to_bits(v);
+ BigInteger256::from_bits_le(&b).to_bytes_le()
+ }
+ /// for a given byte array, returns its bits representation in finite field elements
+ pub(crate) fn bytes_to_f_vec_bits(b: Vec) -> Result, Error> {
+ use num_bigint::BigUint;
+ let bi = BigUint::from_bytes_le(&b);
+ let bi = BigInteger256::try_from(bi).unwrap();
+ let bits = bi.to_bits_le();
+ Ok(bits
+ .iter()
+ .map(|&e| if e { F::one() } else { F::zero() })
+ .collect())
+ }
+ /// interprets the given vector of finite field elements as a vector of bits
+ pub(crate) fn f_vec_to_bits(v: Vec) -> Vec {
+ v.iter()
+ .map(|v_i| {
+ if v_i.is_one() {
+ return true;
+ }
+ false
+ })
+ .collect()
+ }
+}
 +
+ +
+