mirror of
https://github.com/arnaucube/blockchainIDsystem.git
synced 2026-02-28 05:16:41 +01:00
08e3915994b8ed44b5baed70bfdf223729e1c48e
blockchainIDsystem
A blockchain based anonymous distributed login system
Main concept
The objective is to guarantee a decentralized login system, but making sure that registered users are real ones and there are no bots generating large amounts of accounts. Only the verified (by email or phone) users can generate an anonymous ID (the Public-Key blind signed).
How it works?
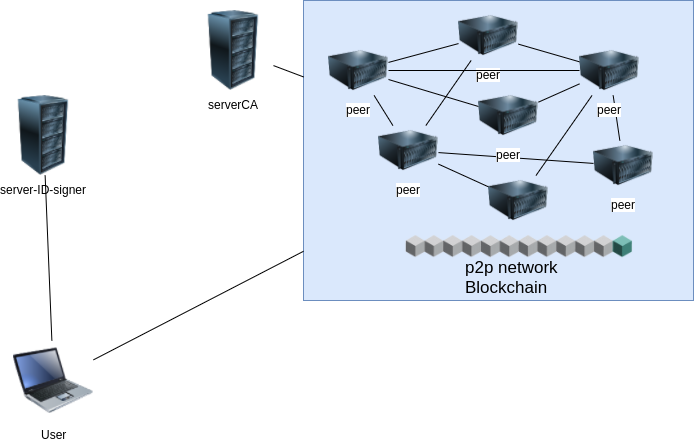
Network infrastructure
There are different types of nodes:
- peers
- the peers of the p2p network that runs the blockchain
- serverCA
- Is a REST server that has been certified (is the Certified Authority) to validate the peers that will be able to participate of the blockchain.
- Have the webapp (frontend) to validate peers through a GUI interface
- server-ID-signer
- The server where the user creates a non anonymous account
- Also is the server that blind signs the Anonymous ID of the users
- Have the webapp (frontend) to interact through a GUI interface
Step by step process
- Once all the nodes of the network are running, a new user can connect to the server-ID-signer.
- The user registers a non anonymous user (using email, phone, password, etc), and performs the login with that user
- The user, locally, generates a RSA key pair (private key & public key)
- The user blinds his Public-Key with the server-ID-signer Public-Key
- The user's Public-Key blinded, is sent to the server-ID-signer
- The server-ID-signer Blind Signs the Public-Key blinded from the user, and returns it to the user
- The user unblinds the Public-Key signed by the server-ID-signer, and now has the Public-Key Blind Signed by the server-ID-signer
- The user sends the Public-Key blind signed to the p2p network
- The peers verify that the Public-Key Blind Signed is correctly signed by the server-ID-signer, if it is, they add the Public-Key to the Blockchain, inside a new block
- Then, when the user wants to login into a platform, just needs to put his Public-Key
- The platform goes to the Blockchain, to check if this Public-Key is registered in the blockchain
- The platform sends a message encrypted with the user Public-Key, and the user returns the message decrypted with the Private-Key, to verify that is the owner of that Public-Key
RSA encryption system
https://en.wikipedia.org/wiki/RSA_cryptosystem
- Public parameters: (e, n)
- Private parameters: (d, p, q, phi, sigma)
- Public-Key = (e, n)
- Private-Key = (d, n)
- Encryption:
- Decryption:
Blind signature process
Languages
Go
56.7%
JavaScript
20.6%
HTML
18.9%
Shell
3.2%
Rich Text Format
0.5%
Other
0.1%